免责声明 本项目的所有内容仅供学习与技术交流使用,旨在帮助开发者理解移动应用的结构和工作原理。
本项目不包含任何针对特定应用的破解操作或侵权内容。 针对某些app存在的简单解包技术内容在各大技术论坛网站均大量存在,并无对这些app造成实际损害 本项目无意协助任何非法用途,包括但不限于绕过版权保护、修改应用功能或获取未经授权的数据。 请确保在使用本项目工具时遵守相关法律法规,并仅用于个人学习或研究目的。
简体中文 | English
hooker是一个基于frida实现的逆向工具包。旨在为安卓逆向开发人员提供一个舒适的命令行界面和一些常用的通杀脚本、自动化生成hook脚本、内存漫游探测activity和service、frida版JustTrustMe、boringssl unpinning全网app通杀
- 1. frida版JustTrustMe,通杀全网APP,且作者一直在持续维护升级
- 2. 自动化生成frida脚本,1秒钟生成一个脚本,脚本备注详细可扩展性强
- 3. 快捷设置socks5代理,无需额外安装socksdroid等三方app实现无感知代理
- 4. 整个使用过程非常舒适的命令行提示,让你享受逆向的过程
手机保证root,无需任何手动启动frida-server等一切配置,hooker会帮你搞定一切 兼容Mac/Linux
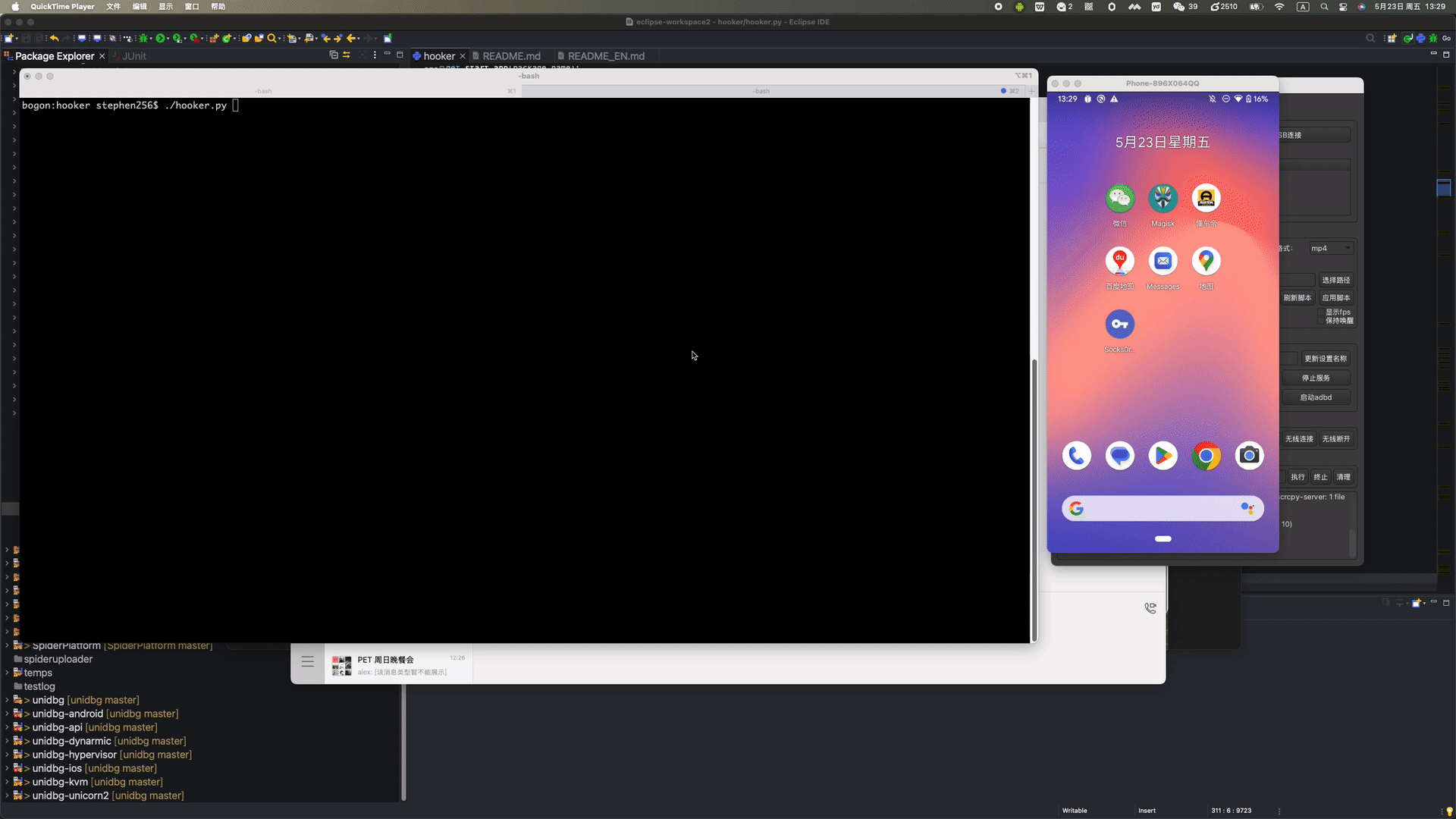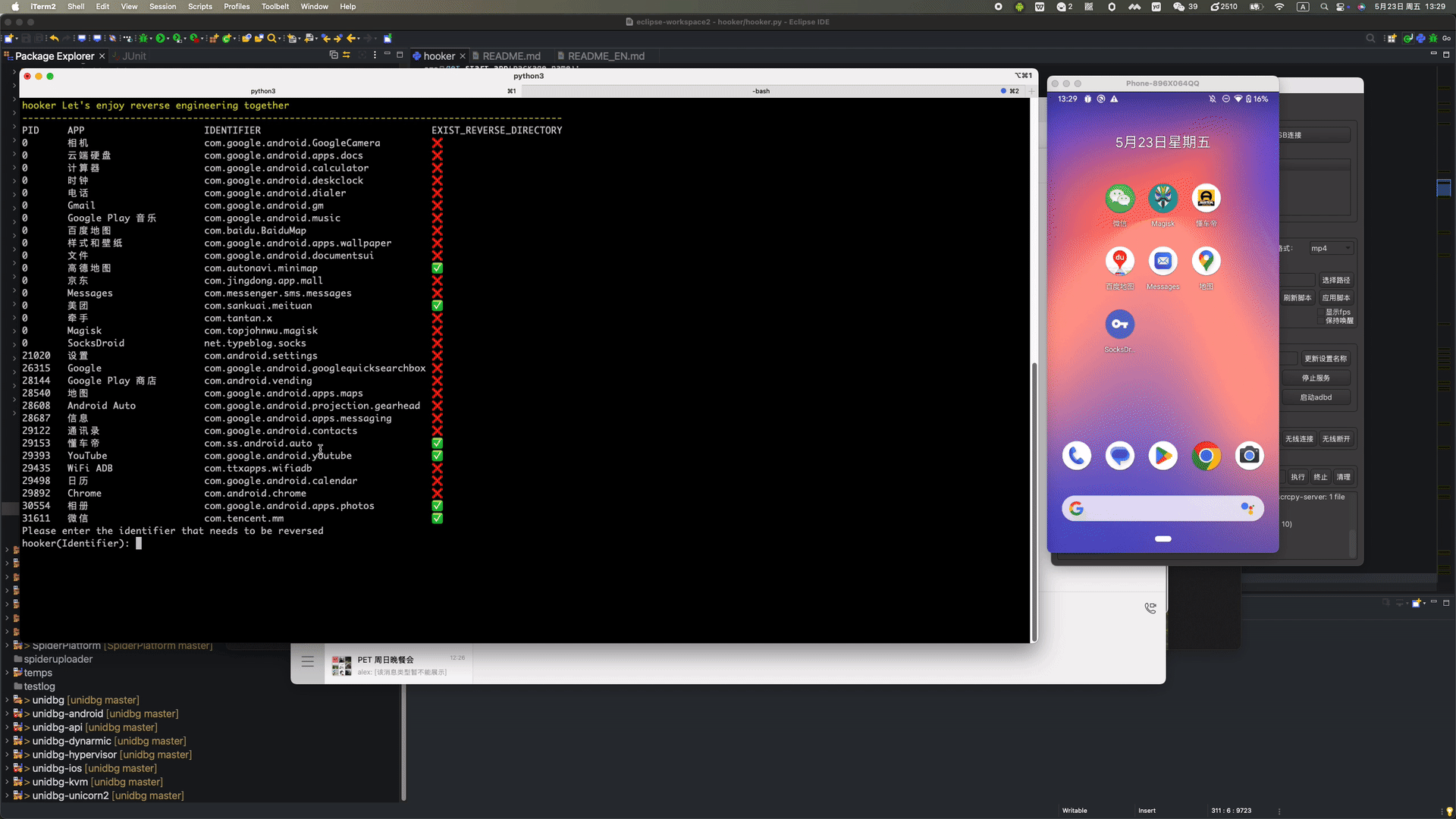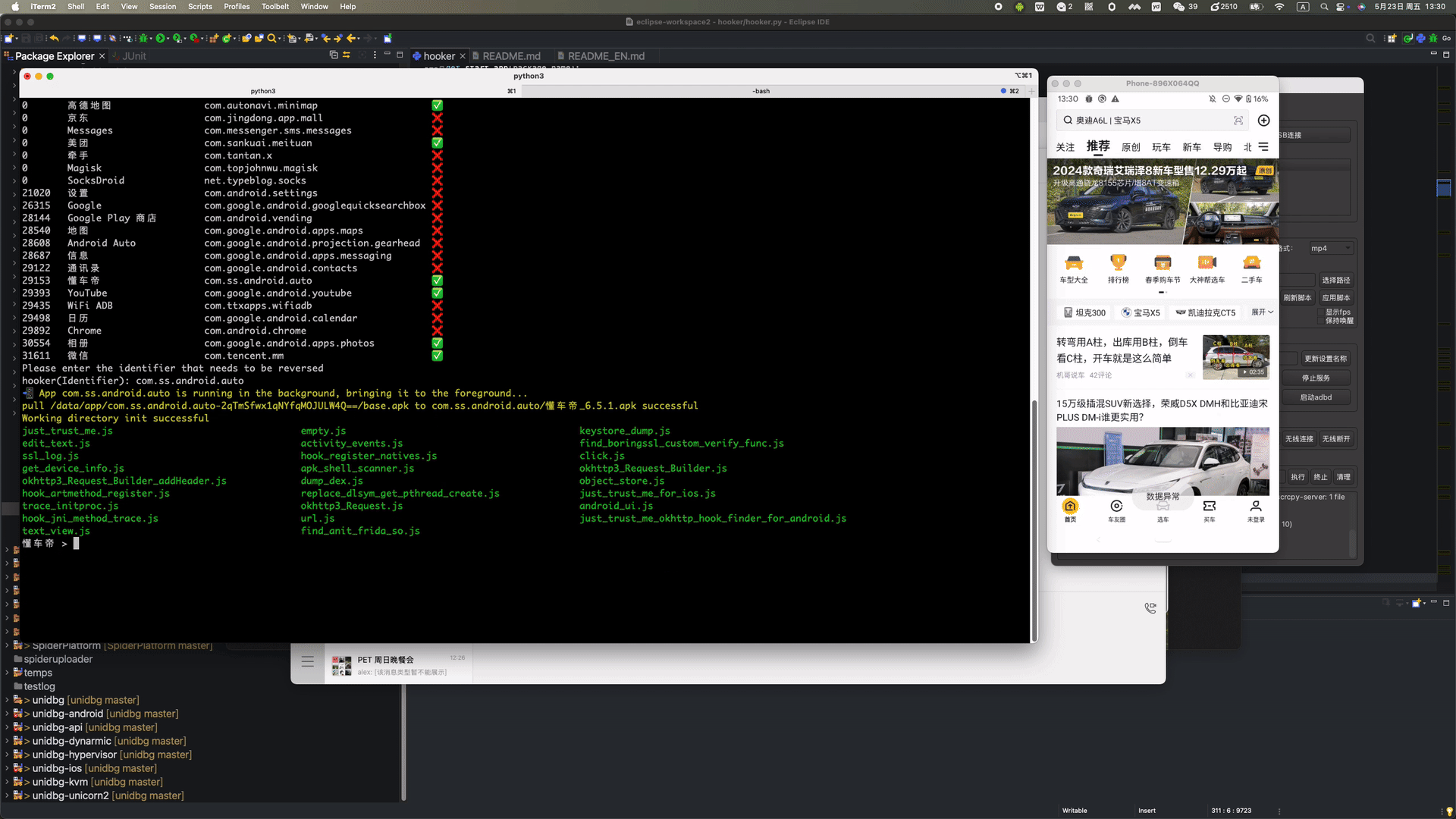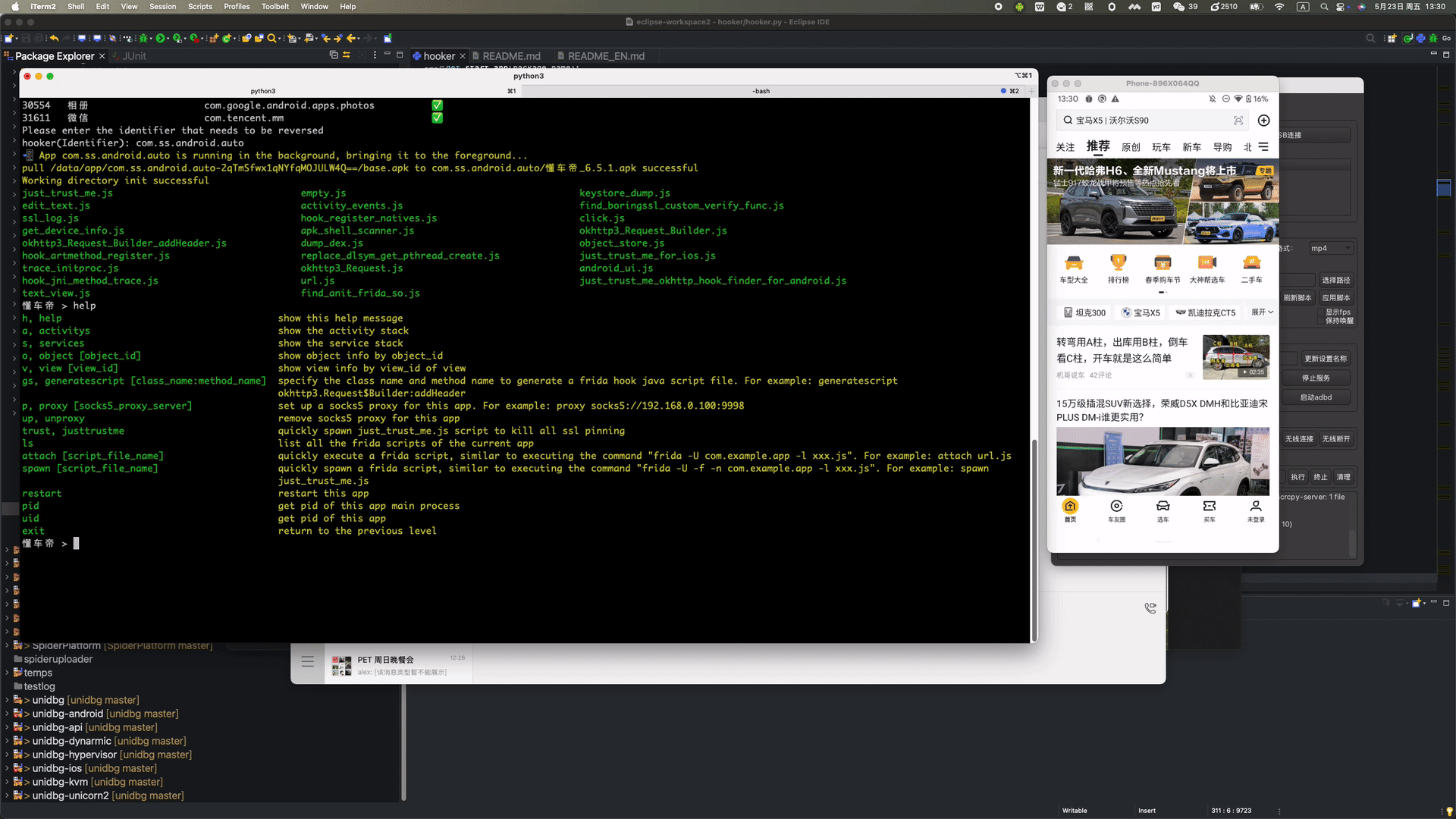
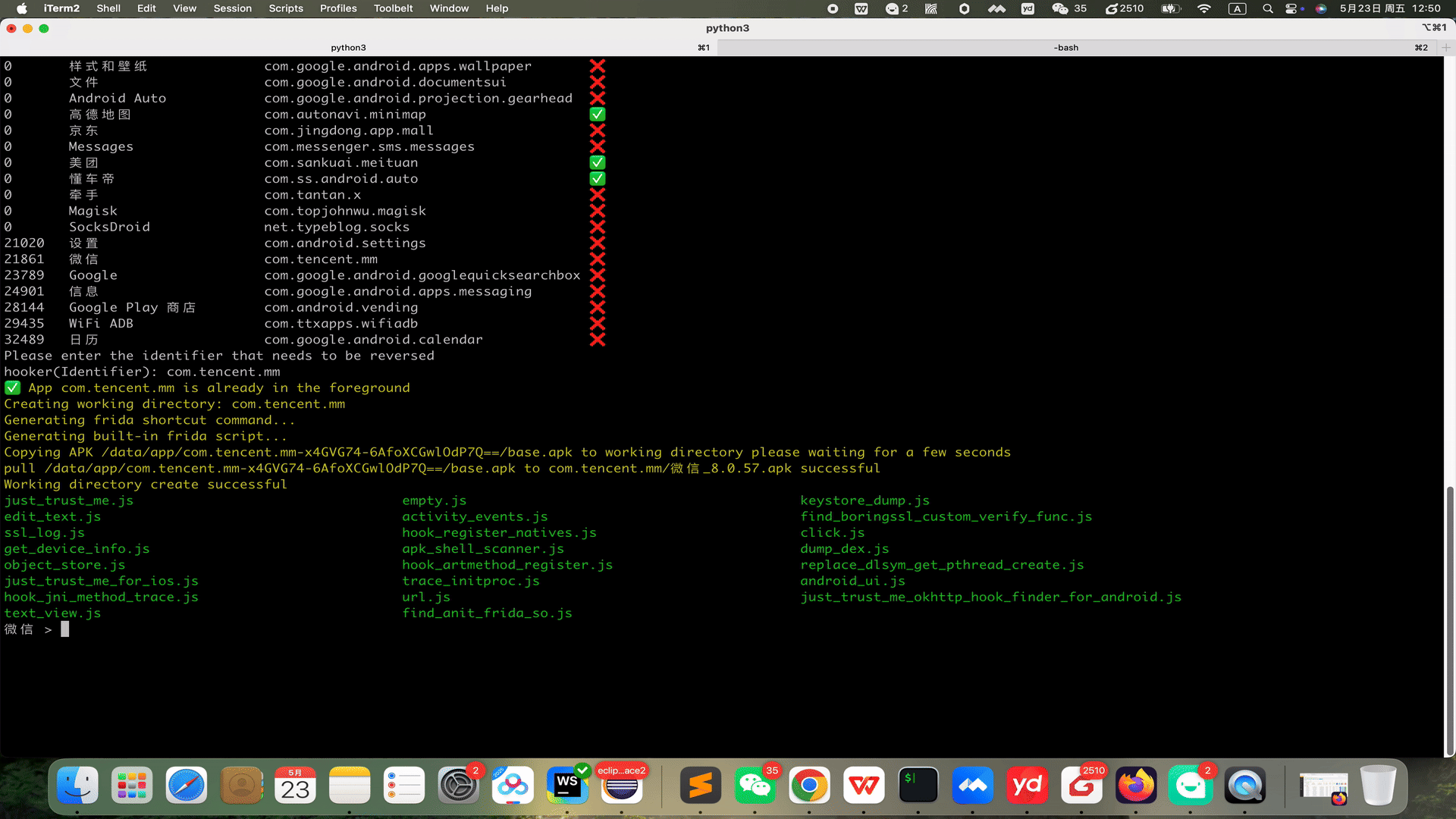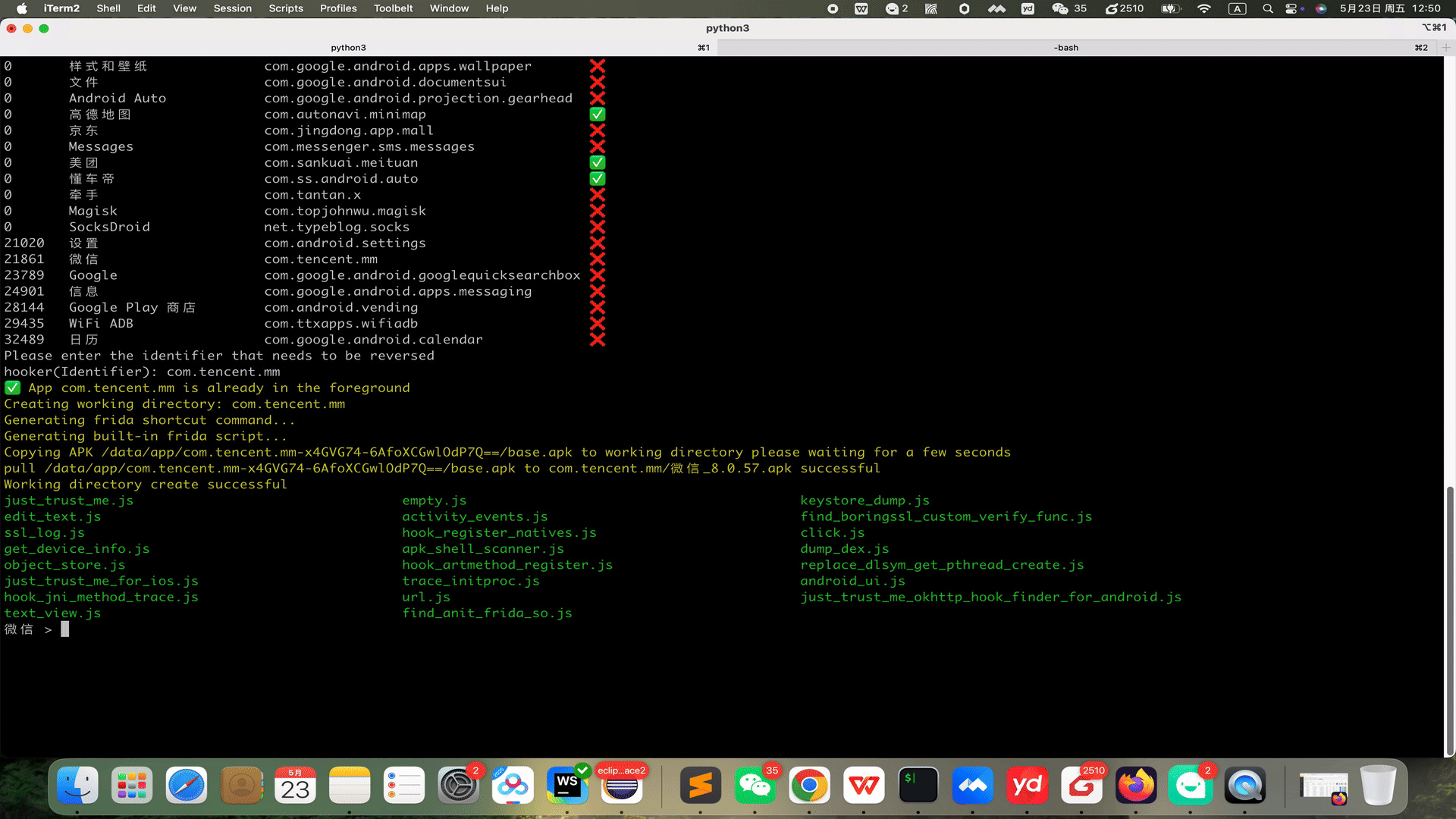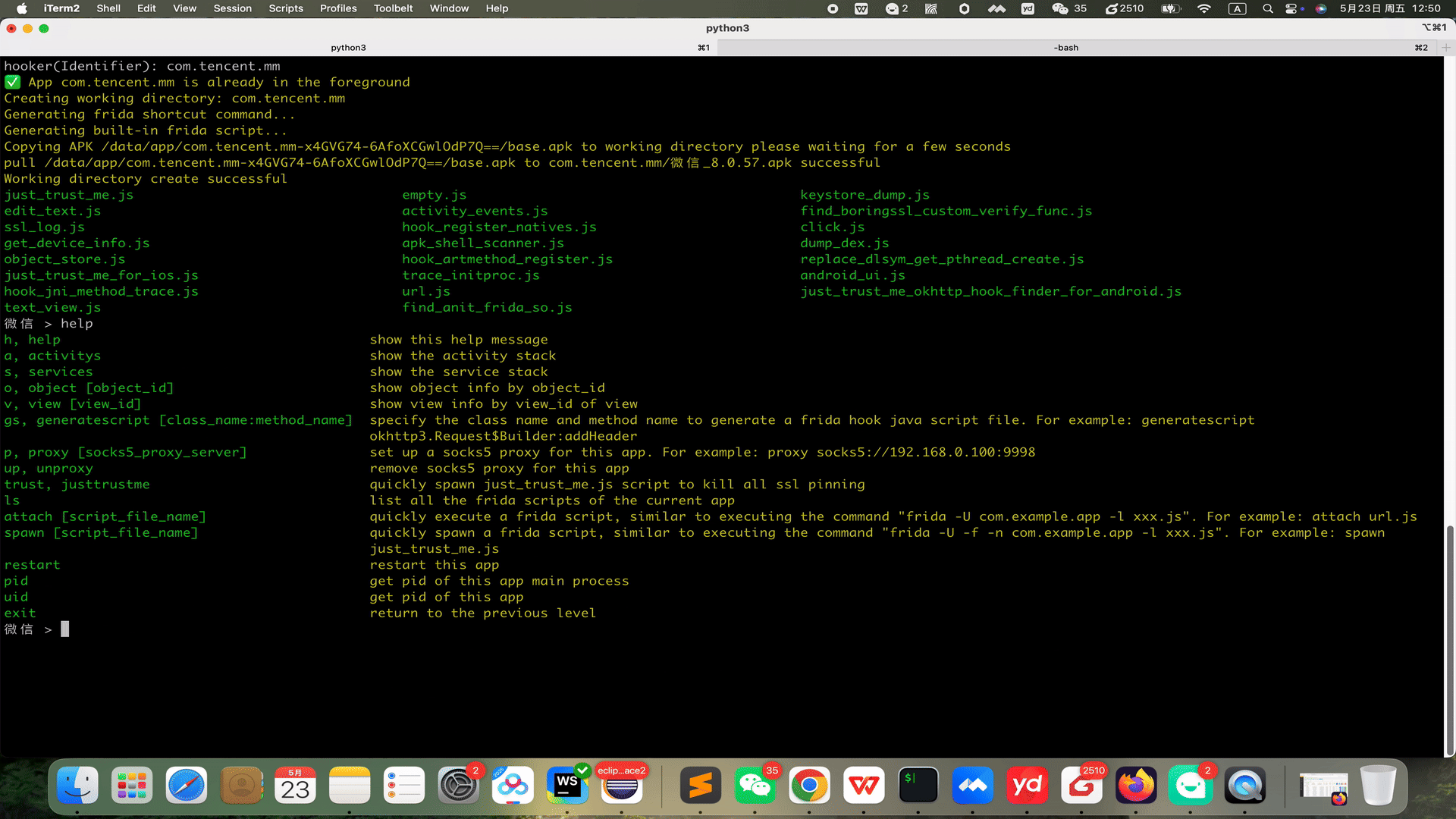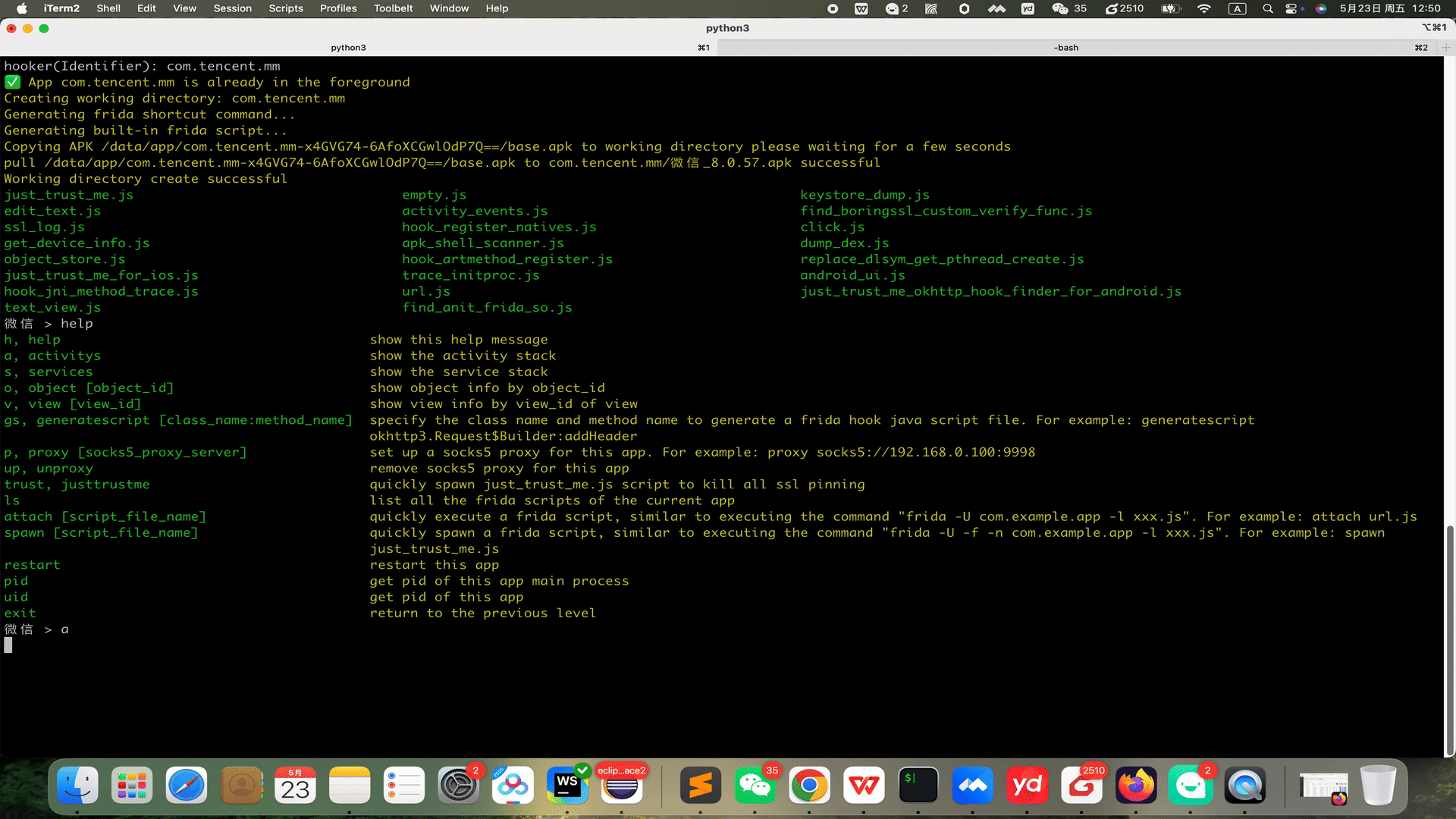
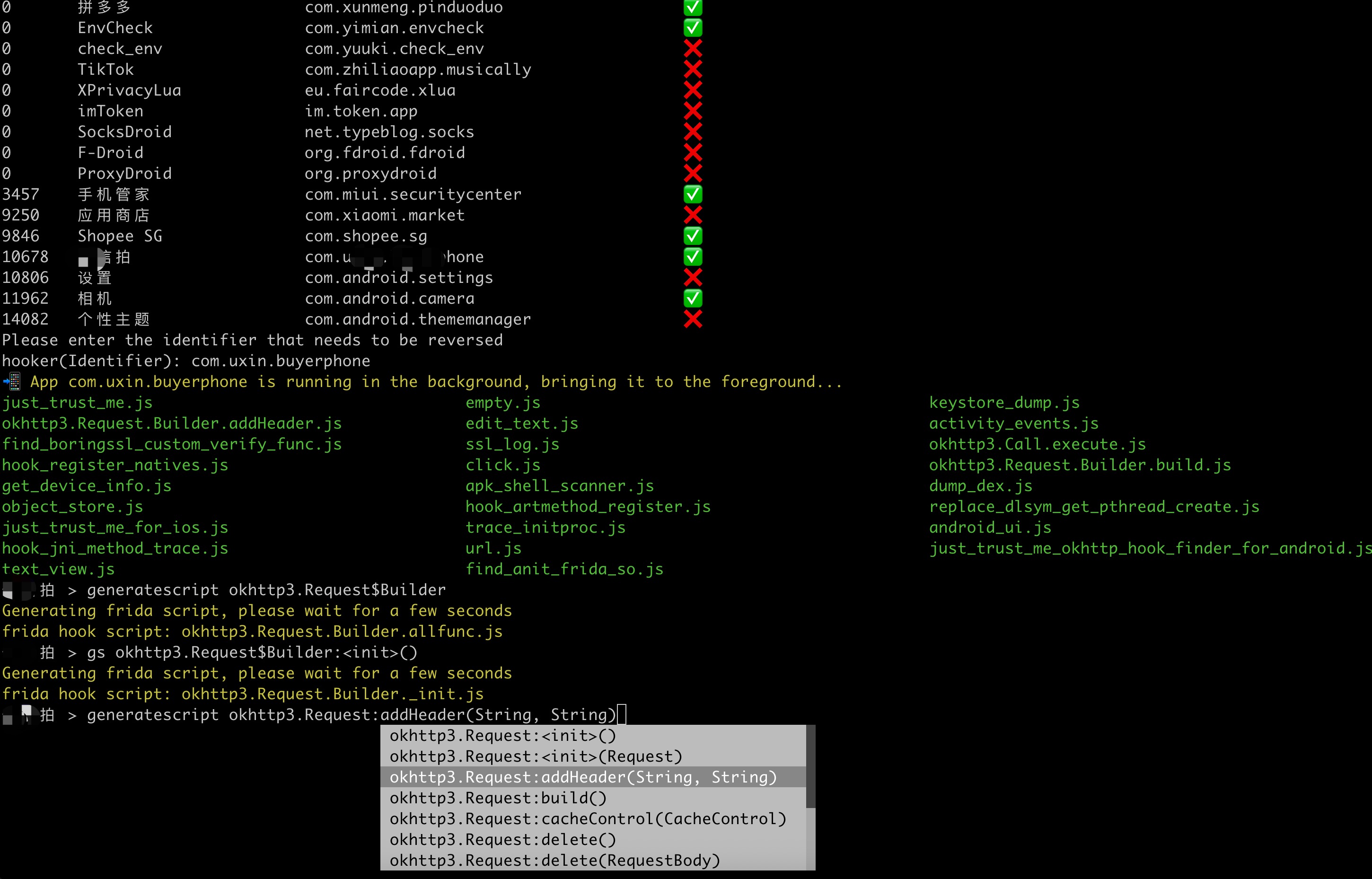
stephen@ubuntu:~$ git clone https://github.com/CreditTone/hooker.git stephen@ubuntu:~$ cd hookerstephen@ubuntu:~/hooker$ pip3 install -r requirements.txtstephen@ubuntu:~/hooker$ adb devices List of devices attached FA77C0301476 devicestephen@ubuntu:~/hooker$ python3 hooker.py bogon:hooker stephen256$ ./hooker.py hooker Let's enjoy reverse engineering together-----------------------------------------------------------------------------------------------PID APP IDENTIFIER EXIST_REVERSE_DIRECTORY0 全球上网 com.miui.virtualsim ❌0 爱奇艺 com.qiyi.video ❌0 红手指云手机 com.redfinger.app ❌0 Reqable com.reqable.android ❌0 美团 com.sankuai.meituan ✅0 得物 com.shizhuang.duapp ❌0 某皮 cxm.shxpxx.sg ✅0 微博 com.sina.weibo ❌0 今日头条 com.ss.android.article.news ✅0 西瓜视频 com.ss.android.article.video ✅0 懂车帝 com.ss.android.auto ✅0 抖音火山版 com.ss.android.ugc.live ✅0 抖音精选 com.ss.android.yumme.video ❌0 淘宝 com.taobao.taobao ✅0 腾讯视频 com.tencent.qqlive ❌0 Termux com.termux ❌0 轻奢 com.tm.bachelorparty ✅0 WiFi ADB com.ttxapps.wifiadb ❌0 VMOS Pro com.vmos.pro ✅0 游戏中心 com.xiaomi.gamecenter ❌0 小米商城 com.xiaomi.shop ❌0 米家 com.xiaomi.smarthome ❌0 小米有品 com.xiaomi.youpin ✅0 小红书 com.xingin.xhs ✅0 运满满货主 com.xiwei.logistics.consignor ✅0 拼多多 com.xunmeng.pinduoduo ✅0 EnvCheck com.yimian.envcheck ✅0 check_env com.yuuki.check_env ❌0 TikTok com.zhiliaoapp.musically ❌0 XPrivacyLua eu.faircode.xlua ❌0 imToken im.token.app ❌0 SocksDroid net.typeblog.socks ❌0 F-Droid org.fdroid.fdroid ❌0 ProxyDroid org.proxydroid ❌3457 手机管家 com.miui.securitycenter ✅3509 优信拍 com.uxin.buyerphone ✅18780 抖音 com.ss.android.ugc.aweme ✅20174 应用商店 com.xiaomi.market ❌20913 设置 com.android.settings ❌30500 小爱同学 com.miui.voiceassist ❌32163 相机 com.android.camera ✅Please enter the identifier that needs to be reversedhooker(Identifier):hooker(Identifier): cxm.shxpxx.sg ✅ App cxm.shxpxx.sg is already in the foreground Creating working directory: cxm.shxpxx.sg Generating frida shortcut command... Generating built-in frida script... pull /data/app/cxm.shxpxx.sg-L8zkrpFVICv0-hOrtmPPxA==/base.apk to cxm.shxpxx.sg/ShopeeSG_3.43.40.apk successful Working directory create successful just_trust_me.js empty.js keystore_dump.js edit_text.js activity_events.js find_boringssl_custom_verify_func.js ssl_log.js hook_register_natives.js click.js get_device_info.js apk_shell_scanner.js dump_dex.js object_store.js hook_artmethod_register.js replace_dlsym_get_pthread_create.js just_trust_me_for_ios.js trace_initproc.js android_ui.js hook_jni_method_trace.js url.js just_trust_me_okhttp_hook_finder_for_android.js text_view.js find_anit_frida_so.js 某皮 >某皮 >help h, help show this help message a, activitys show the activity stack s, services show the service stack o, object [object_id] show object info by object_id v, view [view_id] show view info by view_id of view gs, generatescript [class_name:method_name] specify the class name and method name to generate a frida hook java script file. For example: generatescript okhttp3.Request$Builder:addHeader p, proxy [socks5_proxy_server] set up a socks5 proxy for this app. For example: proxy socks5://192.168.0.100:9998 up, unproxy remove socks5 proxy for this app trust, justtrustme quickly spawn just_trust_me.js script to kill all ssl pinning ls list all the frida scripts of the current app attach [script_file_name] quickly execute a frida script, similar to executing the command"frida -U com.example.app -l xxx.js". For example: attach url.js spawn [script_file_name] quickly spawn a frida script, similar to executing the command"frida -U -f -n com.example.app -l xxx.js". For example: spawn just_trust_me.js restart restart this app pid get pid of this app main process uid get pid of this app exitreturn to the previous level 某皮 >Command语法:gs, generatescript [class_name:method_name]
7.1 生成指定方法的frida hook脚本: gs okhttp3.Request$Builder:addHeader,参数部分(String, String)不是必须写的
某信拍 > gs okhttp3.Request$Builder:addHeader(String, String) Generating frida script, please waitfor a few seconds frida hook script: okhttp3.Request.Builder.addHeader.js 某信拍 >//cat okhttp3.Request.Builder.addHeader.jsJava.perform(function(){varokhttp3_Request_Builder_clz=Java.use('okhttp3.Request$Builder');varokhttp3_Request_Builder_clz_method_addHeader_2grl=okhttp3_Request_Builder_clz.addHeader.overload('java.lang.String','java.lang.String');okhttp3_Request_Builder_clz_method_addHeader_2grl.implementation=function(string,string_x2){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.addHeader(java.lang.String,java.lang.String)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_addHeader_2grl.call(this,string,string_x2);console.log("header name:"+string+" header value:"+string_x2);printBeat(beat);returnret;};});- 7.2 生成指定类的所有成员方法的frida hook脚本: gs okhttp3.Request$Builder
某信拍 > generatescript okhttp3.Request$Builder Generating frida script, please waitfor a few seconds frida hook script: okhttp3.Request.Builder.allfunc.js//cat okhttp3.Request.Builder.allfunc.js//okhttp3.Request$BuilderJava.perform(function(){varokhttp3_Request_Builder_clz=Java.use('okhttp3.Request$Builder');varokhttp3_Request_Builder_clz_method_header_ng3n=okhttp3_Request_Builder_clz.header.overload('java.lang.String','java.lang.String');okhttp3_Request_Builder_clz_method_header_ng3n.implementation=function(string,string_x2){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.header(java.lang.String,java.lang.String)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_header_ng3n.call(this,string,string_x2);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_cacheControl_q8q5=okhttp3_Request_Builder_clz.cacheControl.overload('okhttp3.CacheControl');okhttp3_Request_Builder_clz_method_cacheControl_q8q5.implementation=function(cacheControl){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.cacheControl(okhttp3.CacheControl)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_cacheControl_q8q5.call(this,cacheControl);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_method_bjk9=okhttp3_Request_Builder_clz.method.overload('java.lang.String','okhttp3.RequestBody');okhttp3_Request_Builder_clz_method_method_bjk9.implementation=function(string,requestBody){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.method(java.lang.String,okhttp3.RequestBody)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_method_bjk9.call(this,string,requestBody);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_head_a5nq=okhttp3_Request_Builder_clz.head.overload();okhttp3_Request_Builder_clz_method_head_a5nq.implementation=function(){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.head()';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_head_a5nq.call(this);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_headers_to5i=okhttp3_Request_Builder_clz.headers.overload('okhttp3.Headers');okhttp3_Request_Builder_clz_method_headers_to5i.implementation=function(headers){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.headers(okhttp3.Headers)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_headers_to5i.call(this,headers);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_post_heaq=okhttp3_Request_Builder_clz.post.overload('okhttp3.RequestBody');okhttp3_Request_Builder_clz_method_post_heaq.implementation=function(requestBody){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.post(okhttp3.RequestBody)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_post_heaq.call(this,requestBody);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_build_rmqx=okhttp3_Request_Builder_clz.build.overload();okhttp3_Request_Builder_clz_method_build_rmqx.implementation=function(){varexecutor=this.hashCode();varbeatText='public okhttp3.Request okhttp3.Request$Builder.build()';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_build_rmqx.call(this);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_patch_hp9u=okhttp3_Request_Builder_clz.patch.overload('okhttp3.RequestBody');okhttp3_Request_Builder_clz_method_patch_hp9u.implementation=function(requestBody){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.patch(okhttp3.RequestBody)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_patch_hp9u.call(this,requestBody);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_url_0owi=okhttp3_Request_Builder_clz.url.overload('java.lang.String');okhttp3_Request_Builder_clz_method_url_0owi.implementation=function(string){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.url(java.lang.String)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_url_0owi.call(this,string);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_removeHeader_uzb9=okhttp3_Request_Builder_clz.removeHeader.overload('java.lang.String');okhttp3_Request_Builder_clz_method_removeHeader_uzb9.implementation=function(string){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.removeHeader(java.lang.String)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_removeHeader_uzb9.call(this,string);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_url_ykbd=okhttp3_Request_Builder_clz.url.overload('java.net.URL');okhttp3_Request_Builder_clz_method_url_ykbd.implementation=function(url){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.url(java.net.URL)';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_url_ykbd.call(this,url);printBeat(beat);returnret;};varokhttp3_Request_Builder_clz_method_delete_dqyl=okhttp3_Request_Builder_clz.delete.overload();okhttp3_Request_Builder_clz_method_delete_dqyl.implementation=function(){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder okhttp3.Request$Builder.delete()';varbeat=newMethodBeat(beatText,executor);varret=okhttp3_Request_Builder_clz_method_delete_dqyl.call(this);printBeat(beat);returnret;};//.......省略N行代码- 7.3 生成指定类的构造方法的frida hook脚本: gs okhttp3.Request$Builder:_ 或者gs okhttp3.Request$Builder:<init>
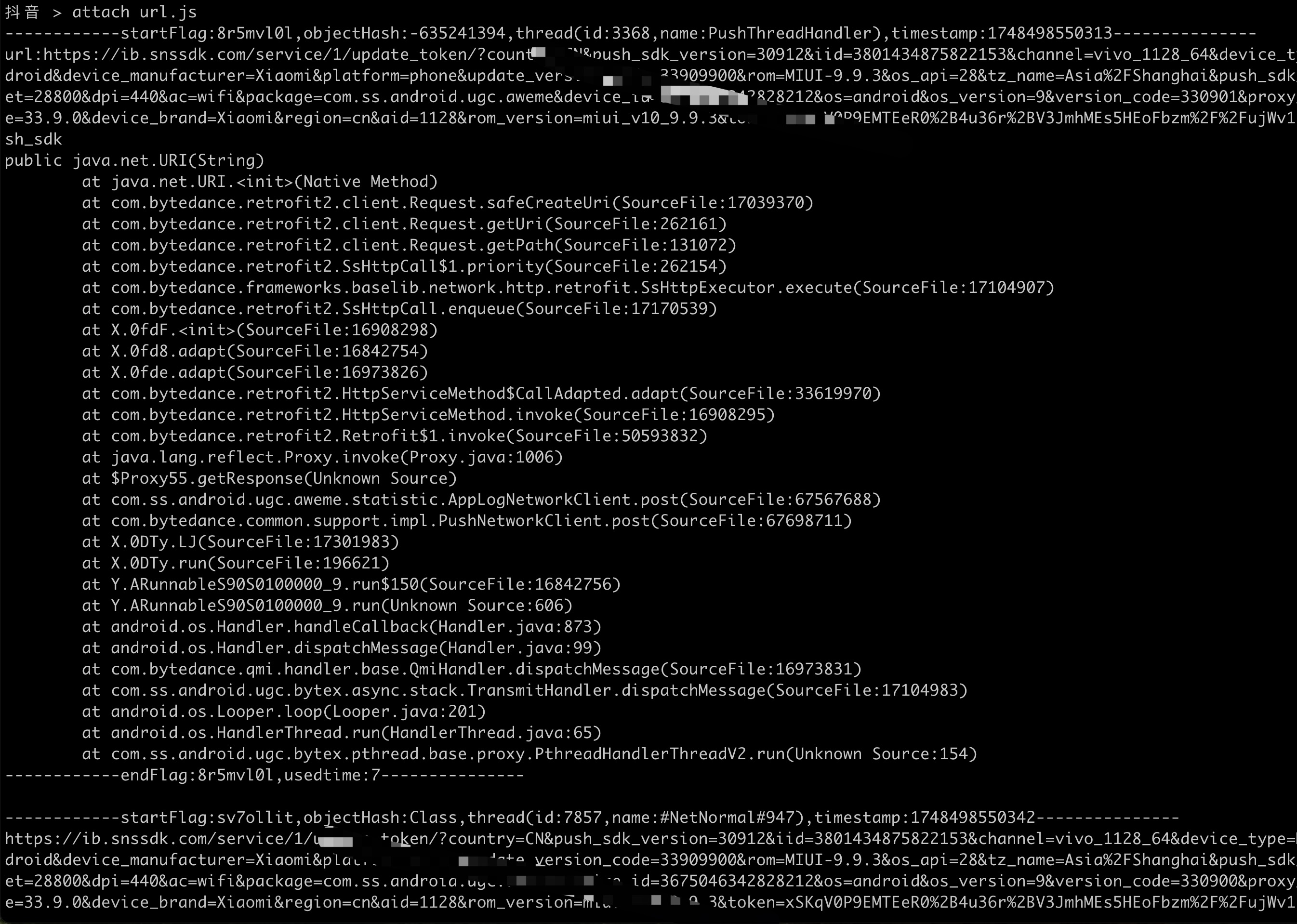
某信拍 > gs okhttp3.Request$Builder:<init>() Generating frida script, please waitfor a few seconds frida hook script: okhttp3.Request.Builder._init.js//cat okhttp3.Request.Builder._init.js//okhttp3.Request$Builder:<init>()Java.perform(function(){varokhttp3_Request_Builder_clz=Java.use('okhttp3.Request$Builder');varokhttp3_Request_Builder_clz_init_uw3i=okhttp3_Request_Builder_clz.$init.overload();okhttp3_Request_Builder_clz_init_uw3i.implementation=function(){varexecutor=this.hashCode();varbeatText='public okhttp3.Request$Builder()';varbeat=newMethodBeat(beatText,executor);varreturnObj=okhttp3_Request_Builder_clz_init_uw3i.call(this);printBeat(beat);returnreturnObj;};varokhttp3_Request_Builder_clz_init_e58t=okhttp3_Request_Builder_clz.$init.overload('okhttp3.Request');okhttp3_Request_Builder_clz_init_e58t.implementation=function(v0){varexecutor=this.hashCode();varbeatText='okhttp3.Request$Builder(okhttp3.Request)';varbeat=newMethodBeat(beatText,executor);varreturnObj=okhttp3_Request_Builder_clz_init_e58t.call(this,v0);printBeat(beat);returnreturnObj;};});某皮 > ls just_trust_me.js empty.js keystore_dump.js okhttp3.Request.Builder.addHeader.js edit_text.js activity_events.js find_boringssl_custom_verify_func.js ssl_log.js hook_register_natives.js click.js get_device_info.js apk_shell_scanner.js dump_dex.js object_store.js hook_artmethod_register.js replace_dlsym_get_pthread_create.js just_trust_me_for_ios.js trace_initproc.js android_ui.js hook_jni_method_trace.js url.js just_trust_me_okhttp_hook_finder_for_android.js text_view.js find_anit_frida_so.js 某皮 >某信拍 > attach url.js ------------startFlag:0755liv1,objectHash:-915348569,thread(id:810,name:Wmda.EventUploadThread),timestamp:1747836814835--------------- url:https://apiwmxx.xxx.com.cn/report/c?api_v=3&sdk_v=1.7.0.0×tamp=1747836814832&appid=17591177894321&p=2&uuid=248056262e0030b7bb56c0f9237f846d public java.net.URL(String) at java.net.URL.<init>(Native Method) at com.wxbx.wmda.e.b.a(SourceFile:5) at com.wxbx.wmda.e.b.a(SourceFile:1) at com.wxbx.wmda.h.a.a(SourceFile:162) at com.wxbx.wmda.h.a.b(SourceFile:19) at com.wxbx.wmda.h.a.a(SourceFile:2) at com.wxbx.wmda.h.a$b.handleMessage(SourceFile:3) at android.os.Handler.dispatchMessage(Handler.java:106) at android.os.Looper.loop(Looper.java:201) at android.os.HandlerThread.run(HandlerThread.java:65) ------------endFlag:0755liv1,usedtime:1--------------- ------------startFlag:1ps6go99,objectHash:-237375819,thread(id:810,name:Wmda.EventUploadThread),timestamp:1747836815192--------------- url:https://apiwmxx.xxx.com.cn/report/c?api_v=3&sdk_v=1.7.0.0×tamp=1747836815188&appid=17591177894321&p=2&uuid=248056262e0030b7bb56c0f9237f846d public java.net.URL(String) at java.net.URL.<init>(Native Method) at com.android.okhttp.HttpUrl.url(HttpUrl.java:327) at com.android.okhttp.Request.url(Request.java:53) at com.android.okhttp.Request$Builder.build(Native Method) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.newHttpEngine(HttpURLConnectionImpl.java:377) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.initHttpEngine(HttpURLConnectionImpl.java:332) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.connect(HttpURLConnectionImpl.java:124) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.getOutputStream(HttpURLConnectionImpl.java:258) at com.android.okhttp.internal.huc.DelegatingHttpsURLConnection.getOutputStream(DelegatingHttpsURLConnection.java:218) at com.android.okhttp.internal.huc.HttpsURLConnectionImpl.getOutputStream(HttpsURLConnectionImpl.java:26) at com.wxbx.wmda.e.b.a(SourceFile:14) at com.wxbx.wmda.e.b.a(SourceFile:1) at com.wxbx.wmda.h.a.a(SourceFile:162) at com.wxbx.wmda.h.a.b(SourceFile:19) at com.wxbx.wmda.h.a.a(SourceFile:2) at com.wxbx.wmda.h.a$b.handleMessage(SourceFile:3) at android.os.Handler.dispatchMessage(Handler.java:106) at android.os.Looper.loop(Looper.java:201) at android.os.HandlerThread.run(HandlerThread.java:65) ------------endFlag:1ps6go99,usedtime:0--------------- // 这里省略无数日志............. ------------startFlag:i7osxvjl,objectHash:134280600,thread(id:810,name:Wmda.EventUploadThread),timestamp:1747836815193--------------- url:https://apiwmxx.xxx.com.cn/report/c?api_v=3&sdk_v=1.7.0.0×tamp=1747836815188&appid=17591177894321&p=2&uuid=248056262e0030b7bb56c0f9237f846d com.android.okhttp.Request.Builder.build() at com.android.okhttp.Request$Builder.build(Native Method) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.newHttpEngine(HttpURLConnectionImpl.java:377) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.initHttpEngine(HttpURLConnectionImpl.java:332) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.connect(HttpURLConnectionImpl.java:124) at com.android.okhttp.internal.huc.HttpURLConnectionImpl.getOutputStream(HttpURLConnectionImpl.java:258) at com.android.okhttp.internal.huc.DelegatingHttpsURLConnection.getOutputStream(DelegatingHttpsURLConnection.java:218) at com.android.okhttp.internal.huc.HttpsURLConnectionImpl.getOutputStream(HttpsURLConnectionImpl.java:26) at com.wxbx.wmda.e.b.a(SourceFile:14) at com.wxbx.wmda.e.b.a(SourceFile:1) at com.wxbx.wmda.h.a.a(SourceFile:162) at com.wxbx.wmda.h.a.b(SourceFile:19) at com.wxbx.wmda.h.a.a(SourceFile:2) at com.wxbx.wmda.h.a$b.handleMessage(SourceFile:3) at android.os.Handler.dispatchMessage(Handler.java:106) at android.os.Looper.loop(Looper.java:201) at android.os.HandlerThread.run(HandlerThread.java:65) ------------endFlag:i7osxvjl,usedtime:1--------------- // 这里省略无数日志.............某音 > proxy socks5://10.112.99.11:9998 proxy socks5://10.112.99.11:9998 OK 某音 >某音 > justtrustme Package name: com.ss.xxxx.xxx.aweme android.security.net.config.NetworkSecurityTrustManager.checkPins('java.util.List') was hooked! android.security.net.config.NetworkSecurityTrustManager.checkPins('java.util.List') was hooked! android.security.net.config.NetworkSecurityTrustManager.checkPins('java.util.List') was hooked! android.security.net.config.NetworkSecurityTrustManager.checkPins('java.util.List') was hooked!javax.net.ssl.TrustManagerFactory.getTrustManagers() was hooked! javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked!javax.net.ssl.TrustManagerFactory.getTrustManagers() was hooked! javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked!javax.net.ssl.TrustManagerFactory.getTrustManagers() was hooked! javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked! javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! static void com.android.org.conscrypt.Platform.checkServerTrusted(javax.net.ssl.X509TrustManager,java.security.cert.X509Certificate[],java.lang.String,com.android.org.conscrypt.AbstractConscryptSocket) throws java.security.cert.CertificateException was hooked! okhttp3.internal.tls.OkHostnameVerifier.verify('java.lang.String', 'javax.net.ssl.SSLSession') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! okhttp3.CertificatePinner.check('java.lang.String', 'java.util.List') was hooked! // 这里省略无数日志.............某信拍 > spawn just_trust_me.js Package name: com.xxx.buyxxphone javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked!javax.net.ssl.TrustManagerFactory.getTrustManagers() was hooked! javax.net.ssl.SSLContext.init('[Ljavax.net.ssl.KeyManager;', '[Ljavax.net.ssl.TrustManager;', 'java.security.SecureRandom') was hooked! // 这里省略无数日志.............某音 > unproxy unproxy OK 某音 >某信拍 > restart restarts com.xxx.buyxxphone某信拍 > uid 10189 某信拍 > pid 3509hooker更新频繁,平均日更约10次。upgrade帮助您随时同步最新代码和相关文件到本地。
MacBook-Pro-32G-2T:hooker stephen256$ python3 hooker.py upgrade Upgrading hooker Repository updated with 'git pull'. Updating mobile-deploy/libext64.so Updating mobile-deploy/libext.so Updating mobile-deploy/libevent-2.1.so Please restart hooker该脚本会 hook 应用中 构造 URL 或 URI 对象的多个关键方法,用于打印或分析网络请求相关的信息(如目标 URL)
Hook 的目标方法 java.net.URI(String) 构造函数
java.net.URL(String) 构造函数
okhttp3.Request.Builder.build() 方法(常用于创建 HTTP 请求)
com.android.okhttp.Request.Builder.build()(系统自带 okhttp)
android.net.Uri.parse(String) 方法(处理 URI 的常用工具方法)
推荐命令:frida url.js
frida版本的just_trust_me,支持boringssl unpinning,理论上支持全网所有app,除非像美团一样做了登录风控抓不了。
在hooker命令行模式封装了快捷命令justtrustme 这在上文 执行justtrustme kill掉所有ssl验证有介绍
亦可直接执行脚本 spawn just_trust_me.js 
当你需要跟踪start某个Activity启动时可执行,获取startActivity的intent信息和调用堆栈。
推荐命令:frida activity_events.js
跟踪点击事件时可执行,并获取被点击View的真实View ClassName
推荐命令:frida click.js
封装一些操作原生Android UI的函数。如startActivity(activityName)、home()、back()、finishCurrentActivity()、clickByText(text) 等等,命令使用得用attach './attach android_ui.js' 原理是借助radar.dex作为代理操作Android原生View。
推荐命令:frida android_ui.js
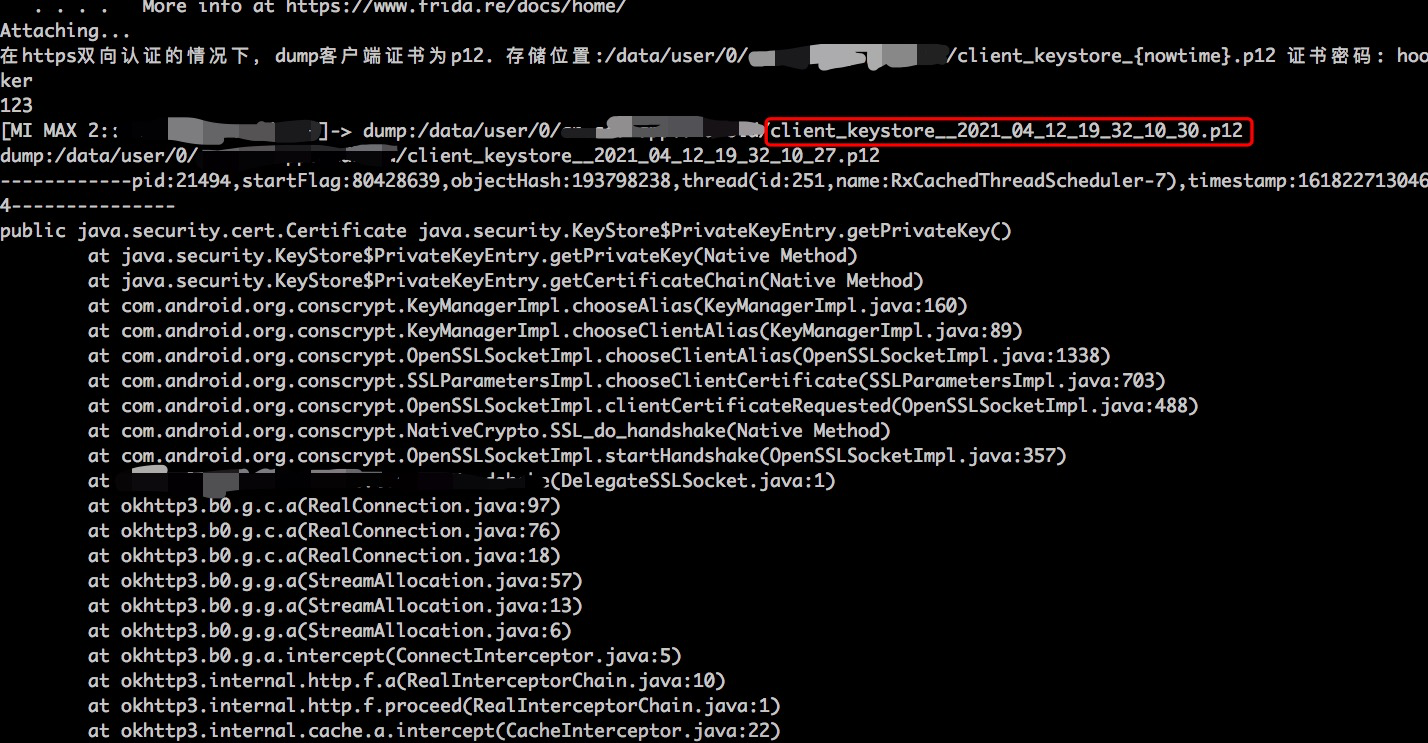
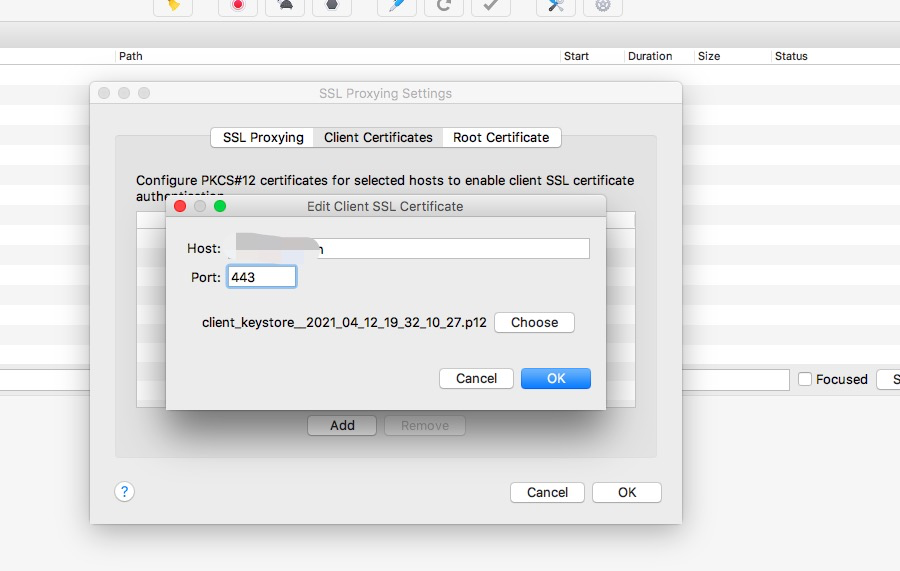
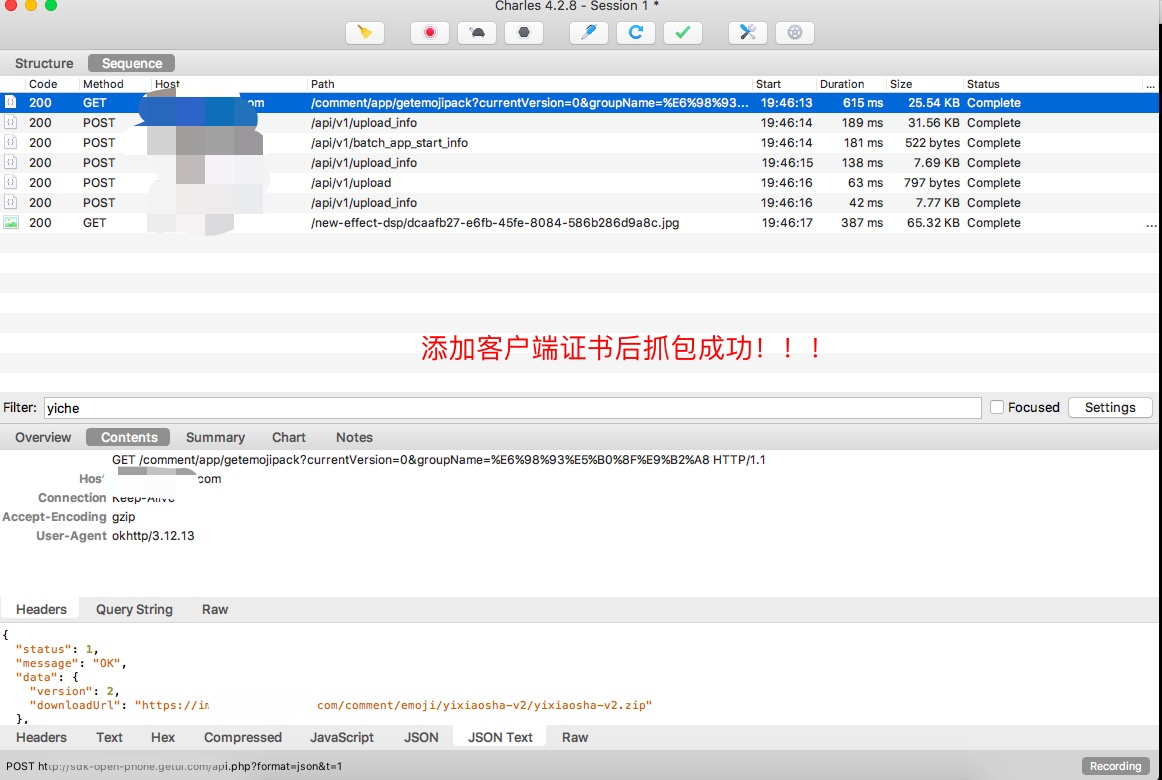
在https双向认证的情况下,dump客户端证书为p12。存储位置:/data/user/0/{packagename}/client_keystore_{nowtime}.p12 证书密码: hooker。原理是hook java.security.KeyStore的getPrivateKey和getCertificate方法,因为客户端向服务发送证书必调这个方法。强烈建议keystore_dump.js用spawn模式启动,
推荐命令:spawn keystore_dump.js
跟踪获取Editview的getText()事件,并获取Editview的真实Class(很重要)。Editview一般绑定Search Action的实现代码,如果你抓取“搜索”接口。那么这个一定可以帮助你定位发送搜索请求的相关代码。
推荐命令:frida edit_text.js
trace JNI register_natives函数
推荐命令:spawn hook_register_natives.js
Ctrl + U:整行清空
Ctrl + W:删除一个单词
Ctrl + K:从光标删到行尾